Evil ISPs can disrupt Communication between Bitcoin Nodes

ETH Zurich scientific and technical researchers are working with Aviv Zohar (from the Hebrew University in Israel) to underscore attacks on Bitcoin through the Web’s routing infrastructure. This is a problem for the crypto currency’s developers because they cannot control the magnitude and direction of those attacks. The esteemed Border Gateway Protocol (BGP) illustrates how packets are transmitted around the world wide web.
Border Gateway Protocol
The problems of BGP are recognized in a simpler generation. It was designed to trust information it obtains. A sloppy or malicious admin in an Internet Service Provider (ISP) network or carrier transmits inaccurate or erroneous BGP route information to the worldwide web. These can putconsiderable portions of traffic in a black hole.
Zohar and his ETH partners published a paper and explained this on ETHs website. They showed two ways the BGP can attack BTC which are partition and delay attacks. The positive aspect of said attacks is the need for an insider because this has to take place at the ISP level. However, the attacks can be very serious.
In partition attacks, the black hole will prevent the two sides from communicating with each other if the ISP is the only passage between huge chunks of the BTC platform. The two islands will continue to process transactions and mine new Bitcoin. Once the Evil ISP connects the islands together again, there is no choice but to get rid of conflicting Bitcoin transactions and blocks on one side.
Delay attacks are more spiteful since researchers say these cannot be detected. This is how they work:
- Nodes A and B present the same Block to a victim Node C.
- Node C requests the Block through GETDATA from Node A. The attacker alters the content so it triggers the transmission of an older Block from Node A. This block is delivered successfully.
- The attacker sets off delivery by changing another GETDATA message generated by Node C 20 minutes after the original block request.
- The Block is sent prior to the 20-minute break. The victim does not disengage from Node A.
Delay attacks affect merchants by making them vulnerable to double-spend attacks. Miners squander processing power while ordinary nodes are not capable of circulating or dispersing the most recent Blockchain version. One issue is BTC nodes gather at few ISP networks. 60% of BTCs traffic is seen only on three ISPs, while 13 ISPs host roughly 30% of the whole crypto currency network.
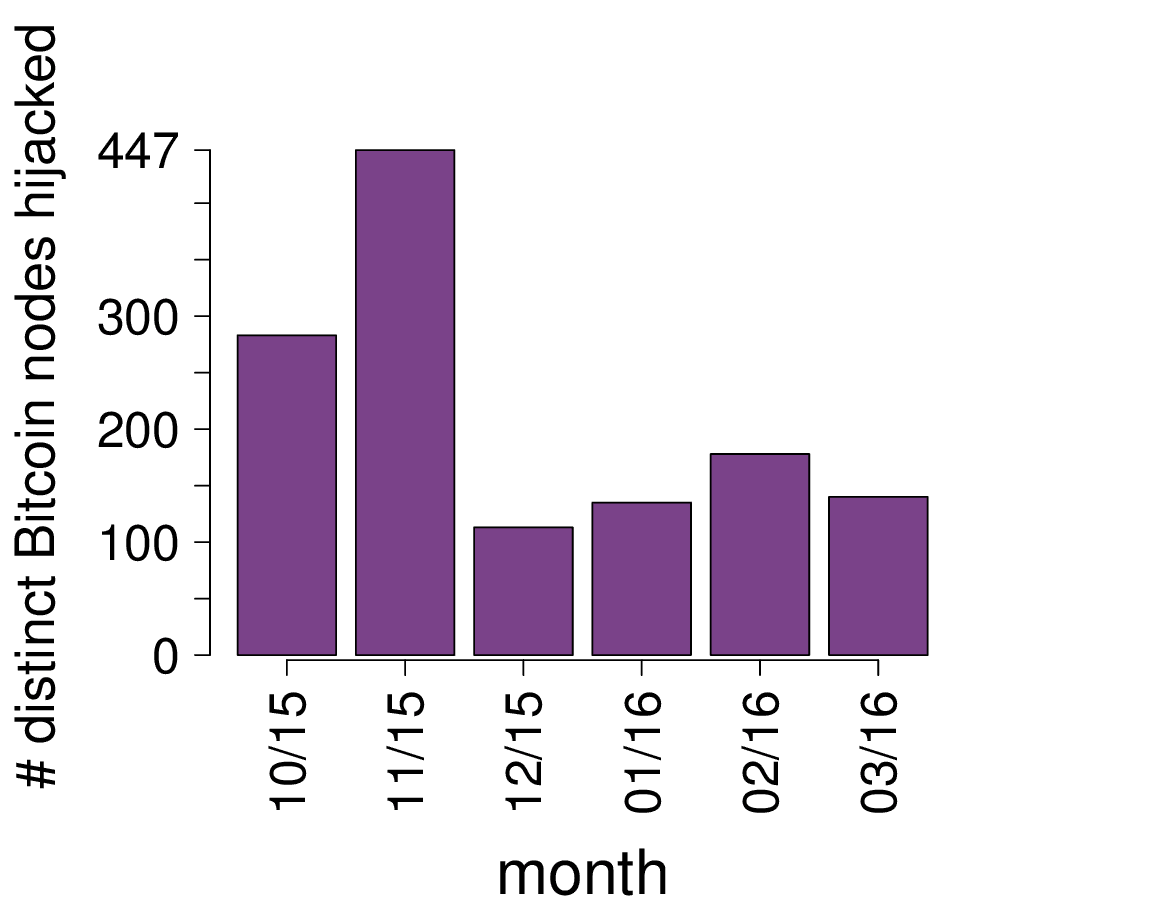
According to the researchers, BGP hijacking (intentional or not) affects up to a hundred Bitcoin nodes monthly. In November 2015, there was a peak of approximately eight percent of the network, with a total of 447 nodes that experienced traffic hijacking.
IEEE Symposium
This work will be presented during the IEEE Symposium on Security and Privacy scheduled for May this year in San Jose, California. Zohar and his partners will release the GITHUB that offers a trial code for this delay attack.
The IEEE has been the major forum for the presentation of developments in Computer Security and Electronic Privacy since 1980. It also gathers practitioners and researches involved in this field for regular consultations. The 2017 Conference marks the 38th yearly meeting of this flagship talk. It will be held at the Fairmont Hotel from May 22nd until May 24th. The workshop is scheduled for the following day.
IP Routing Protocol
BGP is a standard protocol for exterior gateways that facilitates the exchange as well as routing of information among independent systems on the world wide web. It is a vector path program that is also sometimes called as distance vector protocol. It makes routing decisions depending on network policies, paths or rules-sets arranged by a network administrator. BGP is involved in the implementation of core-routing processes.
The Exterior Gateway Protocol (EGP) is a vector routing platform. Routers swap network information such as sets of addresses they can reach with their closest neighbours. This also includes the next address data to be transmitted to those addresses. It differs from link-state Interior Gateway Protocol (IGP) which exchanges topology (referring to geometric properties) information and computes their own directions locally.
EGP floods accessible information though the web. Hence, each EGP router has a direction-finding table that contains address prefixes covering the whole public internet. It does not have anything to do with the end-to-end route but simply the next jump along the course. The path where data is sent is selected based on comparison of all accessible jumps.
Hijacking Bitcoin
Bitcoin is often at the receiving end of attacks since it is the most successful virtual currency. In the paper, “Hijacking Bitcoin: Routing Attacks on Crypto Currencies by Maria Apostolaki, Aviv Zohar, and Laurent Vanbever” the authors explained that autonomous systems have the capacity to catch and control a big portion of BTCs traffic.
It presented the initial nomenclature or classification of routing attacks along with their effects on Bitcoin. The authors took into consideration small attacks, targeting of individual nodes, and big attacks that target the network as a whole. They pinpointed two primary properties that make routing attacks functional, being routing control efficiency and major centralization of BTC with regards to mining and routing.
Network attackers can hijack a small number of BGP prefixes to cut off 50 percent of the mining power. Attacks can also slow down block proliferation considerably by hindering primary Bitcoin messages.
The probable damage to Bitcoin is a concern to users and other stakeholders. A huge amount of mining power may be wasted, which causes substantial loss in revenues or enables double-spending.
Source: Read Full Article