The Startup Looking to Prevent Hackers From Stealing ICO Funds
Initial Coin Offerings (ICOs) are currently big business in crypto. With over $1.2 billion raised in them through-out 2017 alone, according to the financial technology analytics firm Autonomous NEXT, it would be safe to assume that ICOs are doing very well in terms of raising funds from the cryptocurrency community.
ICOs held in Ethereum’s blockchain, with assistance from its smart contract feature, have been receiving a lot of attention lately, an event that works in par with Ethereum’s price rise. The way an ICO works, in simple terms, would be described by a few actions. Developers first present an idea and provide potential investors with an Ethereum address linked to a smart contract. Then, Ethereum users that send Ether to that address are rewarded with an ERC-20 token for participating in the ICOs smart contract.
Due to the amount of money ICOs receive through, they’ve not been left alone by parties with malicious intentions. The process described above means that unless developers find a way to broadcast their smart contract addresses securely to the world, money could end up being funneled to malicious third parties after a phishing-style attack.
This is what happened to CoinDash, a new startup that recently held an initial coin offering. Hackers somehow managed to get access in the backend of CoinDash’s website and changed the address potential investors were sent to send their funds to. This simple trick exploited the investors and ended in $10 million worth of Ether stolen. This means that more than half of the proceedings raised for Coindash ended up in the hands of hackers.
This really isn’t the first time Ethereum users are hit with a major theft in the process of a token sale either. Last year, The DAO hack that came as a result in vulnerabilities in its smart contract was the largest cryptocurrency heist with millions worth of Ether lost. Hackers ended up getting a hold of so many coins that it was ultimately resulting in a hard fork of Ethereum’s blockchain in an effort to save investor funds.
Since that time, there has been some standardization in how ICOs are held and new documentation is helping developers know how to better handle token issuance. After The DAO, vulnerabilities in smart contract code have been mitigated to a better degree, but it’s often the weakest link that gets attacked.
Provided that raising money publicly puts the efforts of developers on public display, it just adds up to the pressure of setting up an entire procedure to raise money from the general public in a distributed way. Thankfully, the overlooked detail that led to CoinDash’s ICO theft is easily covered with simple precautions.
In a recent blog post, the startup, Enigma, that will also be hosting an ICO soon, described their preferred best practices for Ethereum token sales. It’s recognized that the problem -in general- stems from centralization. In CoinDash’s case, users had to trust a single, central source for where to send their funds to for the token sale, their website. This puts a large bulls eye target on what ended up being the weakest link in this token sale.
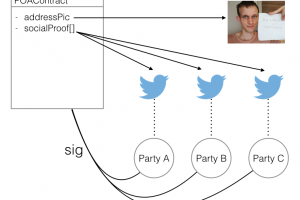
Enigma is pointing out that proof of address needs to be standardized, and a single source for verifying the token sale address isn’t enough. Their proposal is to use a medium that utilizes real world identities (like twitter) through a smart contract in Ethereum’s blockchain for identity verification.
As described in the blog post, this smart contract would have the funding address hard-coded in its creation, marking it signed by receiving transactions from the required parties. Said parties are set to be trusted members of the Ethereum community and their identity would be tied to a blockchain address through public tweets. This signing secures the smart contract in a multi-signature style fashion, and makes it prohibitively harder for attackers to switch the funding address.
Enigma also highlighted that secure passwords and good password practices on social media accounts are additional measures developers of Initial Coin Offerings should take very seriously as it’s just another venue hackers could utilize to pretend being the developers of a token sale in order to redirect funding.
Finally, in an effort to help the community, Enigma stated that after finishing development of their proof of address contract, they’re going to open source it. Such a tool would be especially helpful in dealing with such attacks in the future and standardizing a more secure procedure for raising funds in Ethereum’s blockchain by squashing another potential weak link in the process. The open sourcing of the contract would also enable other parties to review its code and improve upon or adapt it for their needs to secure other projects.
Source: Read Full Article
